

Although most people aren't interested in how to "hack." They are interested in how NOT to be "hacked." Knowing a little of the former can help with the latter.
One of the most widely-read cyber security news sites on the Web, Dark Reading is now the most trusted online community for security professionals. Its community members include thought-leading security researchers, CISOs, and technology specialists, along with thousands of other security professionals.
HAVE YOU BEEN HACKED?

Visit this website to check if your account has been hacked

Google One monitors the dark web for data breach exposes info like SSN, date of birth, and phone number.

Visit this website to check if your email address and other personal data have been made public on the Internet.
SCANNING THE INTERNET OF THINGS?

Check the security of your favorite Password.

BitWarden is an Open Source (FREE) Password Manager.

SuperGenPass is a different kind of password solution that uses a hash algorithm to transform a master password into unique, complex passwords for Web sites.
HACKED WILLINGLY?
These Companies know more about you than any government. Google and Facebook have options to turn off most of this trackingSAFER ON INTERNET
The ultimate in privacy calls for the TOR browser, a VPN connection, and end-to-end Encryption. However, there are easier techniques for average user to get a modicum of privacy.
Set your browser to Incognito mode to hide browsing history.

Google One's VPN protects multiple devices for our online privacy and security on Android, iOS, Windows, and Mac

Use DuckDuckGo for private searches without Google
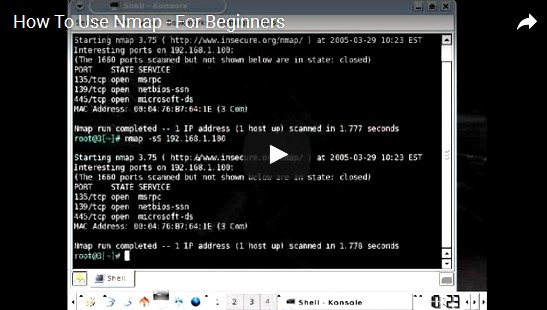
Network Mapper, named “Security Product of the Year” by Linux Journal, uses raw IP packets to discover a network’s configuration, such as available hosts, offered services, running operating systems, type of firewalls.
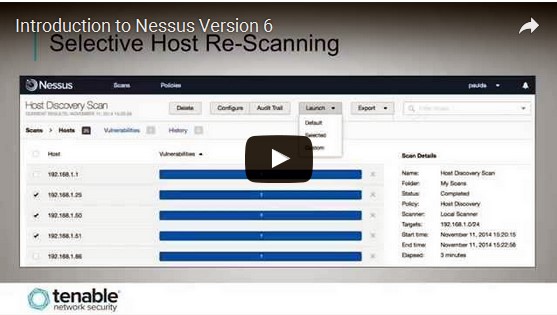
Nessus is the most popular vulnerability scanner in the world. It scans for flaws that would allow a remote hacker to control or access a system, such an incorrectly configured network, failure to change default passwords, and common passwords and missing passwords.
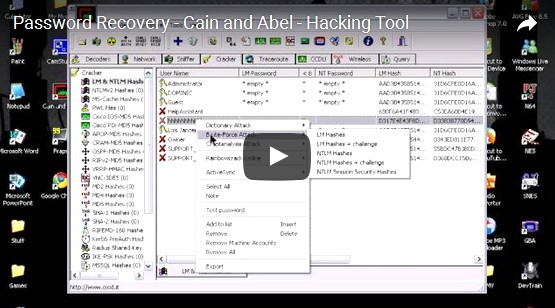
Cain and Abel is a password recovery tool that can capture and monitor network traffic for passwords, crack encrypted passwords using multiple methods, record VoIP conversations, and recover wireless network keys.
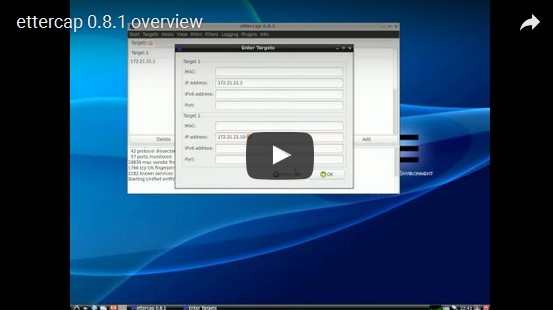
Ettercap is a comprehensive suite for man-in-the-middle attacks on LAN. It can sniff live connections and monitor content on the fly by either filtering packets based on IP addresses, filtering packets based on MAC addresses, putting the network interface into promiscuous mode, or by ARP poisoning the target machines..
The web server scanner Nikto can check for potentially dangerous files, for outdated versions of servers, and for Server version-specific issues. It looks at server configuration concerns such as multiple index files and various HTTP server options, and attempts to identify installed web servers and software.

Wireshark is a de-facto standard packet analyzer. It shows what all users are doing on the network and gives a way of identifying and remedying odd traffic that could be linked to a Trojan. Data can be derived from a live network connection or read from a file of already-captured packets.
NirSoft web site provides a unique collection of small and useful freeware utilities.
- Password-recovery tools.
- Network tools
- View IP adrs & other info
(Updated every week).
See also: Video Streaming Capture Tools, Windows Registry Tools, and Domain/IP Lookup Tools